
START HERE: Training Video 6.1a Product, Service and Process Design
CEP21tm
21st Century
County of Excellence
OE21 Guideline: 6.2b
Security and Cybersecurity
Protect organization from loss of sensitive information to outside sources
Strategic Objective:
Strategic Objective:
Ensure information management systems reliability, availability & cybersecurity
Quality Objective:
Quality Objective:
Responsibility:
Lead: Operations Focus Team (OFT) Support: Other focus teams
Approved by: (Name) Chair, Leadership Focus Team (LFT)
Approved: DD-MMM-YY
VALUE ADDED
1. Ensure reliability and availability of information systems (hardware and software)
2. Ensure security of information systems and the data they house
3. Protect information, intellectual property, and other and assets by limiting cyberattacks and events
4. Minimize impact on the organization from cyberattacks and events
POLICY 6.0 COMMENTARY
The organization has adopted the Baldrige Framework Item 6.2b Security and Cybersecurity, and 7.1b(2) Emergency Preparedness Results as the internal policy, including the following sub-items:
6.2b(1) Reliability - The organization ensures the reliability of its information systems.
6.2b(2) Security and Cybersecurity - The organization ensures the security and cybersecurity of sensitive or privileged data and information, including management of electronic and physical data and information to ensure confidentiality and appropriate access, including:
-
Maintaining awareness of emerging security and cybersecurity threats;
-
Identifying and prioritizing information technology systems to secure from cybersecurity attacks;
-
Protecting information systems from cybersecurity attacks; and
-
Detecting, responding to, and recovering from cybersecurity breaches.
7.1b(2) Emergency Preparedness Results - The organization tracks current and trends in key measures or indicators of the effectiveness of preparedness for disasters or emergencies (including cybersecurity breaches).

6.2b Flow Diagram (Figure 6.2b-1 Management of Information Systems)
Inputs to 6.2b Management of Information Systems
-
6.2b-OFT-S1 Cybersecurity (survey)
-
6.2b-OFT-D1 Cybersecurity Framework (.pdf)
-
Internal organization tools for security and cybersecurity (if any are used)
Measurement and Analysis Tools and Techniques
-
6.2b-OFT-S1 Cybersecurity Analysis (.xlsx)
Outputs from 6.2b Management of Information Systems
Milestone 1 - Management Information Systems Requirements
Milestone 2 - Framework for Improving Critical Infrastructure Cybersecurity
Milestone 3 - Cybersecurity Assessment
Milestone 4 - Process Chart for Security and Cybersecurity Excellence
Milestone 5 - Update Strategy Plan and Metrics
Implementation Instructions
START IMPLEMENTATION
Task 6.2b-1 - Define Requirements for Reliability/Security/Availability of Information Systems - The Leadership Focus Team (LFT) ensures the reliability and availability of the organization's computer (hardware) and the software used. The organization computers (hardware) are protected from power surges, power loss, water damage, fire damage, adverse weather (storms), unauthorized intruders, software/program availability, and other risks as specified in OE21 4.2 Information and Knowledge Management (Task 4.2.5). After these Information System requirements are fully documented and approved, they are published on the organization's INTRANET.
-
PROGRESS: You have reached Milestone 1 (good work). Input the status [20%] on the organization's OE21 Intranet Main page alongside the title of this standard.
Task 6.2b-2 - Study Framework for Security and Cybersecurity - The Leadership Focus Team (LFT) uses the Framework for Improving Critical Infrastructure Cybersecurity (Version 1.0 National Institute of Standards and Technology, February 12, 2014), and applies the following cybersecurity definitions:
-
CYBERSECURITY - The process of protecting information and assets by limiting the occurrence of, detecting, and responding to attacks.
-
CYBERSECURITY EVENT - A cybersecurity change that may have an impact on organizational operations (including mission, capabilities, or reputation).
-
CYBERATTACK - A cyberattack is any type of offensive tactic or maneuver employed by nation-states, individuals, groups, or organizations that targets computer information systems, infrastructures, computer networks, and/or personal computer devices by various means of malicious acts usually originating from an anonymous source that either steals, alters, or destroys a specified target by hacking into a susceptible system. These can be labeled as either a cyber campaign, cyberwarfare or cyberterrorism in a different context. Cyber attacks can range from installing spyware on a PC to attempts to destroy the infrastructure of entire nations. [source: Wikipedia]
This framework is used as a self-assessment tool to enable the organizations to understand the effectiveness of its cybersecurity risk management efforts better, and to help identify strengths and opportunities for improvement in managing cybersecurity risk, based on the organization’s mission, needs, and objectives.
Figure 6.2b-1 (Table 1) Framework for Improving Critical Infrastructure shows the function and category unique identifier items, based on the N.I.S.T. Framework for Improving Critical Infrastructure Cybersecurity. The Framework focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization’s risk management processes.
I'm a paragraph. Click here to add your own text and edit me. It's easy.
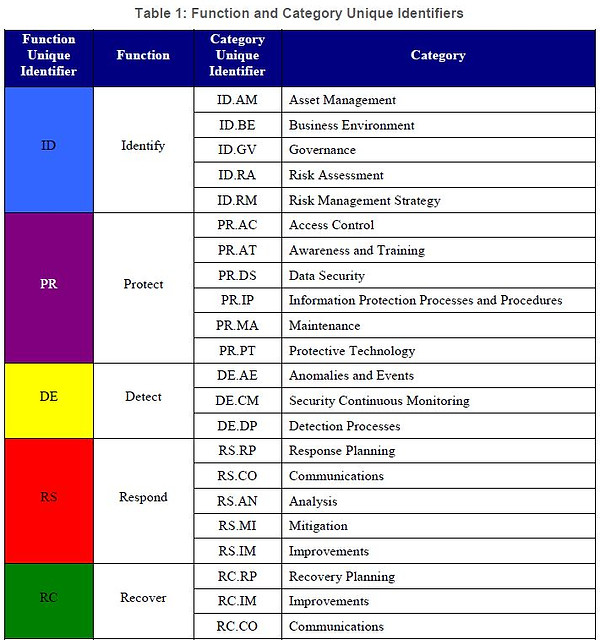
Figure 6.2b-2 - Framework for Improving Critical Infrastructure
The Cybersecurity Framework consists of three parts: the Framework Core, the Framework Profile, and the Framework Implementation Tiers. The Framework Core is a set of cybersecurity activities, outcomes, and informative references that are common across critical infrastructure sectors, providing detailed guidance for developing individual, organizational Profiles.
Through the use of the Profiles, the Framework will help the organization align its cybersecurity activities with its business requirements, risk tolerances, and resources. The Tiers provide a mechanism for organizations to view and understand the characteristics of their approach to managing cybersecurity risk.
NOTICE: If the Cybersecurity Framework is new to the organization, then it may be advisable to seek outside assistance in learning the framework and how it should be applied.
-
PROGRESS: You have reached Milestone 2 (good work). Input the status [40%] on the organization's OE21 Intranet Main page alongside the title of this standard.
Task 6.2b-3 - Conduct CYBERSECURITY ASSESSMENTS - This Assessment is administered by the OFT and facilitator. The Assessment is associated with specific categories and sub-categories as presented 6.2b Table 1 Framework for Improving Critical Infrastructure Cybersecurity.
The key tools used for the Cybersecurity Assessments are:
-
6.2b-OFT-S1 Cybersecurity (survey)
-
6.2b-OFT-S1 Cybersecurity Analysis (.xlsx)
-
6.2b-OFT-D1 Cybersecurity Framework (.pdf)
Table 6.2b-1 presents implementation steps, actions, results, and references for this assessment.

Table 6.2b-1 Implementation of 6.2b Cybersecurity Assessment
Figure 6.2b-3 provides an example of the OE21 Cybersecurity Assessment Dashboard

Figure 6.2b-3 OE21 Cybersecurity Assessment Dashboard
6.2b-OFT-D1 Cybersecurity Framework (.pdf) is used to interpret and understand the categories (e.g, IDENTIFY (ID) and sub-categories (Asset Management ID AM).
-
PROGRESS: You have reached Milestone 3 (good work). Input the status [60%] on the organization's OE21 Intranet Main page alongside the title of this standard.
Task 6.2b-4 - Create Process for Security and Cybersecurity Excellence - Based upon the results of the OE21 Cybersecurity Assessments, the Leadership Focus Team (LFT), supported by the Operations Focus Team (OFT) use the Process Chart tab in the 6.2b-OFT-S1 Cybersecurity Analysis (.xlsx) sheet. This Process Chart is consistent with the 6.1a-OFT-A Process Designer (.xlsx) model and uses the instructions in OE21 6.1a Product, Service, and Process Design.
The Process Chart steps must meet the N.I.S.T Cybersecurity Framework security and cybersecurity requirements including how the organization:
-
Manages electronic and physical data and information to ensure confidentiality and appropriate access;
-
Maintains organizational awareness of emerging security and cybersecurity threats;
-
Identifies and prioritize information technology systems to secure the organization from cybersecurity attacks or breaches;
-
Protects data and information systems from cybersecurity attacks; and
-
Detects, respond to and recover from cybersecurity breaches.
At this point, the finished Process Chart becomes the official Cybersecurity Process Chart, with steps, responsibilities, and estimates of process time (Pt), and the estimated cost of the process.
Over time, the Cybersecurity Process Chart Pt, Wt, and NVA estimates and cost will be improved and updated based on ongoing Cybersecurity Assessments and actual cybersecurity attack activities.
-
PROGRESS: You have reached Milestone 4 (good work). Input the status [85%] on the organization's OE21 Intranet Main page alongside the title of this standard.
Task 6.2b-5 Integrate Cybersecurity Assessment Action Plans into Operations Excellence Action Plan - Integrate Analysis Action Plans into 6.0-OFT-P Operations Excellence Strategy Plan - The measurement and analysis tools (.xlsx) used in this standard may include tasks added to the (Plan) tabs, or other analysis observations that should require actions. If necessary, these new tasks should be integrated into the Operations Excellence Strategy Plan. This integration of new tasks may require the approval of the added tasks, labor, and non-labor resources, schedules, and revised budgets for the Operations Excellence Strategy Plan.
Task 6.2b-6 - Select 6.2b Management Information and Cybersecurity Metrics.
NOTICE: If the organization has an existing Performance Measurement System (PMS), then the internal process is followed for selection, input, and review of measures associated with this OE21 standard. The following guidelines are suggested for the selection of metrics:
Guideline 1 - Select Key Results Indicators (KRI). The KRIs are commonly called Key Performance Indicators (KPI). Examples of KRIs for 6.2b Management of Information Systems, are as follows:
-
Number of Cyberattacks per Month
-
Cycle time from cyber attack until recovery of information systems and data
Guideline 2 - Table 6.2b-2 provides Metrics selection and review implementation steps, actions, references, and instructions guides.

Table 6.2b-2 Implementation of 6.2b Cybersecurity Metrics
Task 6.2b-7 Review Cybersecurity Metrics into PMS - Conduct regular (at least monthly) reviews of Standard 6.2b Measures. Reviews for KRIs are critical to show whether overall organization performance is moving toward target levels and key intended outcomes (KIO) for Leadership Excellence.
Correlation: Where possible, the KRD (drivers) are correlated with KRI (indicators) to determine if and how much the KRD Action Plans are helping boost KRI performance.
At this point, regular performance reviews are conducted and attended by all OE21 Focus Teams.
Figure 6.2b-4 provides an example KRI for 6.2b Cybersecurity Assessments
PROGRESS: You have reached Milestone 5 (congratulations). Input the status [100%] on the organization's OE21 Intranet Main page alongside the title of this standard.
Figure 6.2b-4 Trend Chart and Action Plan for Cyber Attack Recovery (example)

Figure 6.2b-4 KRI for 6.2b Cybersecurity Assessments Trend (Example
Continue to Guideline 6.2c Safety and Emergency Preparedness